5 Keys to Secure Remote Support
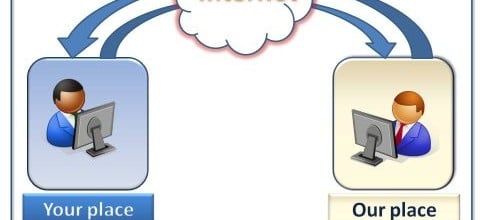
Smartphone usage is increasing on every day, a large number of community usually prefer Smartphones for emails scrolling, collaboration with colleagues and apps downloading as well. People uses such devices so may they can handle work from everywhere. No doubt IT faces challenge to meet such all expectations to enhance users’ productivity as well as for their satisfaction. A large number of organizations are using legacy tools such as VNC and RDP to encourage and help mobile users with mobile support. IT Support companies of Dubai are striving to release your stress for effective results. New innovations are the need to meet the IT needs, IT support is one of them that allow technicians to connect quickly and resolve the problems of users by sitting at their home by maintaining security features.
1. Access
Look for an amazing remote support that clouts identity management systems to server excellent login to the system employing single sign-on and permits techs to sign in secure mode with current authentication modes. One must think to place a specific number of identities needs in an organization and also curtail the number of passwords managed and stored. For gizmo of this level of control as well as access management, see the Server Solutions that influences industry standards for unpretentious integration like SAML.
2. Permission
Remote Support must level up a permission based sample where the end user accepts permission for the technician for remotely access to the device or computer. This works as handclasp between technician and end user.
3. Encryption
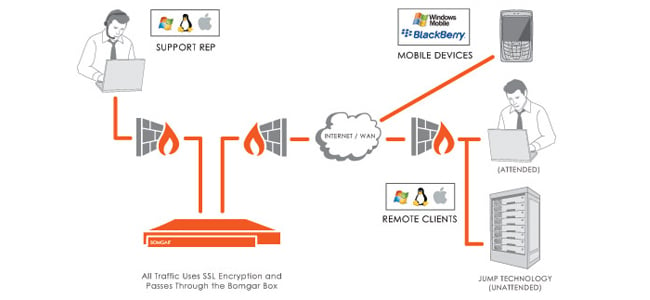
One can ask any time for IT Support from anywhere, VPN’s and servers helps you to connect through internet, far away from the LAN and that connection among user and tech must stand with highest encryption standards possible. A large number of Server Solutions works on public protocols like HTTP to produce a connection. They use to work on particular style of Network Solution so you can enjoy support with full ease.
4. Compliance
Help desks of different sizes needs to provide instantly an audit trajectory of Secure Remote Support activity to give definite compliance of shared IT governance terms and conditions. On security audit occasion one must be able to finalize what machines were retrieved, what issues were solved and some files that were shared.
5. Administration
Whitehats ensures you for Safe mode Remote Support Solution. Administrators need to be able to handle entire support session to get alarmed on which technicians can perform specific tasks. This will control the access of the technicians and also allay data loss and incongruous usage of the system by non-authorized technicians.
Everyone knows Remote Support Solution is the need of this age, comprising this need Whitehats is providing Server Solutions and remote services to clients. Our technicians are expert and can solve your problem at your home. You just need to tell them your problem and next step is of technicians, they highlight issue and resolve it then. They also link up with different connection with a professional Networking Solution.