New Ransomware with Cryptocurrency Mining Capabilities - Everything you need to know
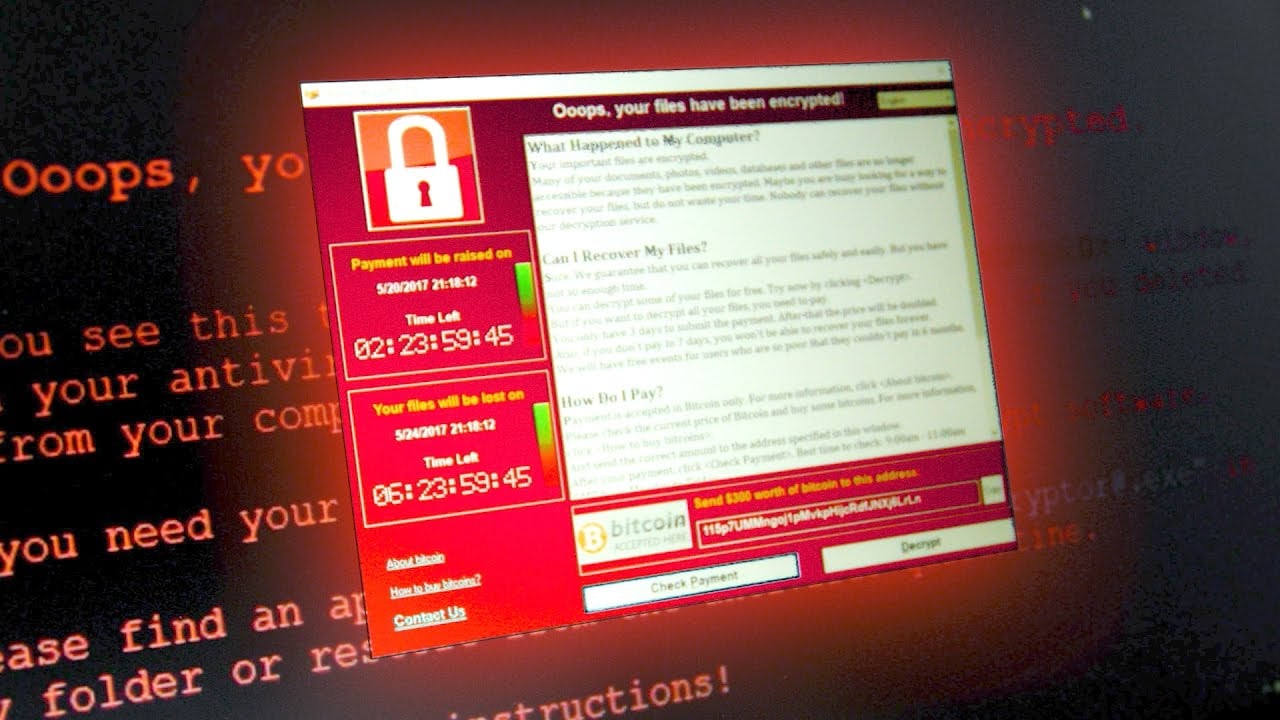
Taking a look back at 2017, we heard a lot about ransomware ( mostly because of two massive global outbreaks of infections). According to a research Bitdefender, the ransomware payments hit $2 billion during the last year that was as much as twice as compared to previous year. Many security researchers warned about more sophisticated and damaging attacks in the future. Today in 2018, we are again hearing about a new type of malware that infects victims systems with either cryptocurrency miners or ransomware, depending on which can be more profitable for attackers.
While ransomware works by locking the victim`s computer and preventing the users from accessing the files until the ransom payment is made, these new variants are capable of mining digital currency by using the CPU power of infected systems.
This Ransomware with cryptocurrency capabilities are top threats so far this year and in many ways, it is replacing the traditional ransomware model that we witnessed in Wanna Cry and Petya outbreaks. As a result, the ransomware attacks directly demanding money to decrypt files in the computer are on the decline while crypto mining based malware infections are on rising. This might be due to the reason companies are more aware of these types of attacks and took measures to deal with such attacks making them less effective and hard to execute. The second reason might be the growing value of the cryptocurrency that has lured hackers to conduct such types of attacks that don’t directly involve in demanding money from victims.
Let`s us have a look at how crypto mining malware attacks work and how to prevent our businesses from these emerging new threat.
You might be interested in our earlier blog post How to prevent your Business from unknowingly become susceptible to Ransomware Attacks?
How Does it Work?
The most recent discovery is a new variant of Rakhni ransomware family malware that is loaded with cryptocurrency mining capabilities.
The new variant of Rakhni malware is delivered to victims computer through spear phishing emails, that includes either attachments or links with MS Word files. These emails encourage victims to download the documents and if opened enable edited as well. The document includes a PDF icon that if clicked launched a malicious executable script on the victim's machine that also prompt fake error message. This misleads the users into thinking that what a system file required to open the document is missing.
This malware performs several tasks while remaining hidden in the background and performs anti-VM and anti-sandbox checks to decide which attack vector to deploy. After the check is performed, it further installs ransomware in case target machine has a “bitcoin” folder in AppData section.
After performing checks, the for which purpose the victim's machine can be used in the better way it encrypts all files with RSA-1024 algorithm while terminating all processes that match the predefined list of most commonly used applications and display ransom message.
In another case, it installs cryptocurrency miner with machines having no Bitcoin folder and have two logical processors. It is completely designed to disguise itself as a trusted process. In addition to that, it collects various types of system information and sends it back to a server controlled by hackers.
Regardless of which attack vector is performed on victim's machine, it is capable of checking if any listed antivirus process is launched and if found nothing it also runs several cmd commands in an attempt to disable Windows Defender.
Do you need help regarding the security of your computer and network infrastructure? Whitehats Network security solutions in Dubai and Antivirus Antispam solutions are designed to help you achieve the maximum level of security of your systems and networks.
How it affects?
As we all know Ransomware can make our system inaccessible for use. This new variant if install crypto mining malware in our system can cause a lot of frustration and problems. The mining process itself requires a lot of system resources to run. Therefore, it makes the system unstable and might result in a crash with the possibility of permanent data loss. In addition to that when the system is running at its peak, it generates lot of heat that under few circumstances like the bad cooling system, high room temperature might damage computer components. This does not here, by having this malware infection your computer become prone to many other types of cyber-attacks that include cross-site scripting, SQL injection, Denial of service, code injection and many others.
How Deal with it?
Right Now, this new variant malware is targeting users in Russia (95%) with small fractions in Kazakhstan (1.30%), Ukraine (.60%) Germany (0.50%) and India (0.40%). Although this malware is restricted to these countries right now it has the potential to become a global epidemic at any time.
Here is what you can deal to minimize the threat.
- You must teach your employees to detect phishing attacks.
- Make them understand, refrain from opening suspicious files and links provided in an email.
- As humans are naturally curious and often ignore this rule, you must implement least privilege administrative rules through access control.
- Get the help you Managed IT service provider to get advice on hardening workstation environment.
- Implement information security policy for your organization, with clearly specified rules and procedures on use of systems, configuration, settings and incidence reporting.
- Implement file integrity monitoring to monitor files related vulnerabilities.
In addition to all above, it`s obvious that you need good antivirus, antimalware and antispam solutions to keep your system protected from such threats.
If you suspect that your computer has been infected by any type Ransomware virus, please disconnect it from your network by removing the network cables from it and give us a call as soon as possible to minimize the loss of information for your company.
Whitehats Network security solutions in Dubai and Antivirus Antispam solutions are designed to help you achieve the maximum level of security of your systems and networks. Need help in protecting your IT infrastructure? Contact us at +971 4 33 82 500 for a free consultation.